This article is the first in a series of articles where the Sutardja Center for Entrepreneurship & Technology takes a basic deep dive into an industry or topic that is at the forefront of startup ideas and opportunities today.
This past week, Yahoo (now owned by Verizon after its highly awaited merger), announced that hackers that had penetrated its network in late 2014 were able to gather information on 500 million users, including their names, email addresses, passwords, telephone numbers and more. Though they clarified that the hackers are no longer ‘believed’ to be able to access their system, the event represents the largest theft of personal data ever. The intrusion came during a period of frequent high-profile hackings, including from companies such as Anthem, MySpace, LinkedIn, Target and Sony – since then, the cybersecurity industry has grown massively, with companies spending millions of dollars to secure their intellectual property, internet platforms and user information. Today, consumers are highly concerned about who has access to their information; having gone through the ‘growth of data’ phase from 2011-2014, where companies focused on easy ways of integrating data, there is no way to trace how many platforms and websites contain a single user’s information, creating the need for individual companies to be highly protective of their data, if they want to keep consumer trust.
Given that we’re in such an era, it is highly important to understand what cybersecurity is, and how it affects us. [Definition] Cyber security involves protecting information and systems from major cyber threats, such as cyber terrorism (cyber terrorism is the disruptive use of information technology by terrorist groups to further their ideological or political agenda), cyber warfare (Cyber warfare involves nation-states using information technology to penetrate another nation’s networks to cause damage or disruption.), and cyber espionage. In their most disruptive form, cyber threats take aim at secret, political, military, or infrastructural assets of a nation, or its people, as well as at monetizable data owned by private companies.
How has cybersecurity changed over the years? Previously, attackers used to largely be creatures of opportunity, looking for the path of least resistance that gave them data – if they encountered secured and protected networks, they were likely to move on and look for softer targets. Today’s cybercriminals are not as defensive; they are highly motivated, well-funded by organizations and structures with agendas, and are more patient in their effort to break into defenses.
[Definition] Malware is malicious software or code that typically damages or disables, takes control of or steals information from a computer system – it may be in the form of adware, backdoors, logic bombs, spyware, Trojan horses or worms (we apologize if that sounds like biology & history more than it does computer science!)
There are various forms of attacks, as defined above – the most prevalent are zero day attacks, that target software vulnerabilities that are yet to be discovered or patched, cloud data leakage which happen when employee uploaded data on servers such as Dropbox and Google Drive are breached or accessible to public and stolen, mobile malware which is specifically intended to steal data on mobile devices (messages, pictures), targeted attacks and SQL injections. The key problem – collectively, advanced malware has outpaced traditional anti‐malware strategies and in the process, has established a foothold within organizations that criminals and nation‐states can use to steal information and attack sensitive assets.
Modern cyberattack strategy has evolved. In addition to direct, open attacks against a high‐value server or asset, today’s attack strategy also employs a patient, multistep, covert process that blends exploits, malware, and evasions in a coordinated attack; these steps include reconnaissance (studying victims and planning attacks, using social engineering, phishing, email address harvesting and other tactics to research and identify targets), weaponization & delivery (determining malware payload, and the method used to deliver it), exploitation, and then installation (which insures persistence of the threat).
To these various forms of attacks, there are a number of prevalent practices for protection – network defenses keep hackers from infiltrating and navigating through corporate networks, endpoint and mobile device protection prevent hackers from compromising individual devices, data in motion defenses protect data while it is being transferred between devices, data at rest defenses protect data when it’s stored in databases & analysis and correlation tools monitor the flow of data to verify that it is being sent or exists only where it should. Each of these defenses represents its own huge industry with a number of players struggling for market share and developing their own versions of solutions for security concerns.
There is an increasing demand for protection against such threats – In 2014, 69% of executives expressed concerned about cyber threats, including a lack of data security, according to a PricewaterhouseCoopers survey. In 2015, an updated survey increased that number to 86%, so it’s clear that the desire for better cybersecurity is not going away anytime soon. Why? The consequences are huge. In addition to commercial losses and public relations problems, disruption of operations and the possibility of extortion, cyber-attacks may also expose an organization to regulatory action, negligence claims, the inability to meet contractual obligations and a damaging loss of trust among customers and suppliers.
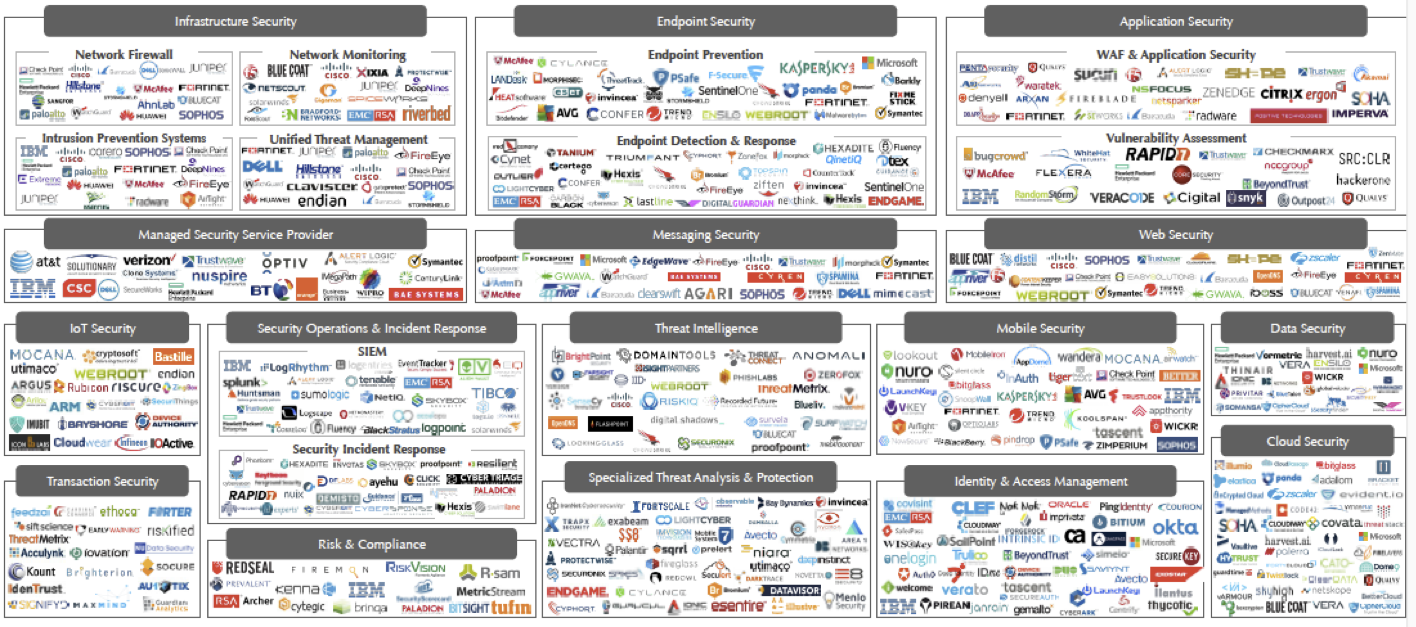
The Market for Cybersecurity? BI Analytics estimates that $655Bn will be spent by companies on cybersecurity initiatives to protect PCs ($386Bn), mobile devices ($113Bn) & IoT devices ($172Bn). Research has repeatedly shown that many IoT device manufacturers and service providers are failing to implement common security measures in their products. According to a poll in 2015, 82% of companies expect to be attacked; only 43% of companies feel prepared to deal with such attacks, showing that there is a large addressable market actively in need of a product. There is a large number of companies existing in various offering categories – these can be viewed in the landscape below. Just to begin with, there are 16 major categories of cybersecurity companies can operate in (they can be considered product categories offered by these companies). The largest cybersecurity companies include IBM, Cisco, FireEye, Microsoft, McAfee, CITRIX, Palo Alto Networks, Symantec and money others.
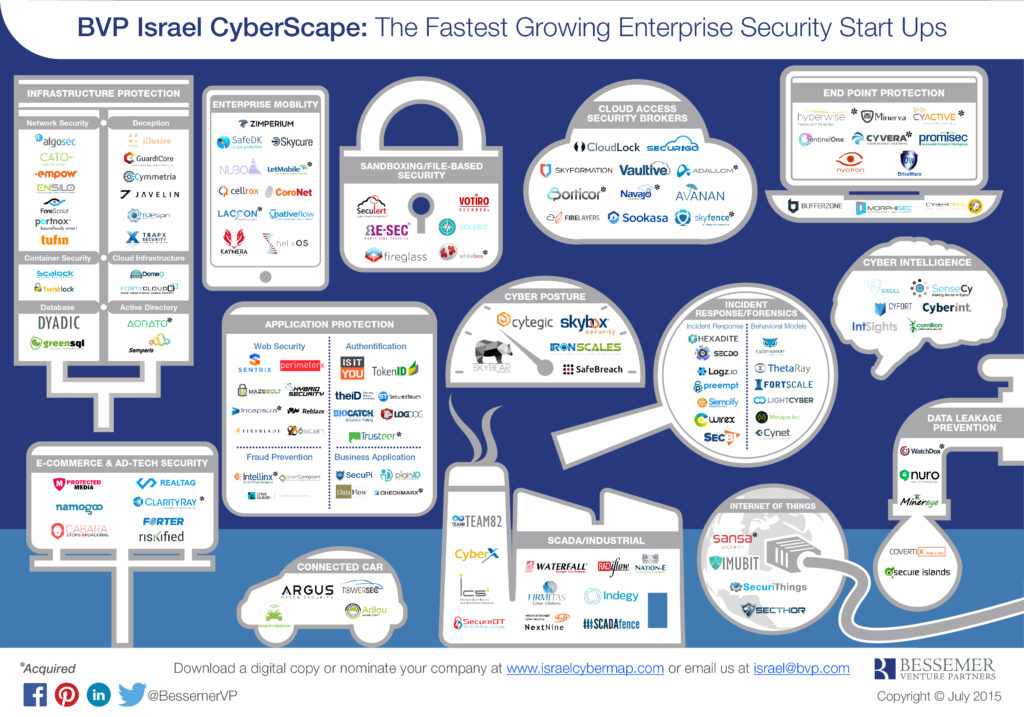
In specific, there is an increasing saturation in cyber security markets by startups themselves in particular. This info graphic shows the saturation of such startups in various markets in just Israel.
One can see clearly that cybersecurity is one of the most important issues prevalent today in the mind of any companies that operate digitally (well, that’s most companies today!). Computer networks have always been a target since it represents the most profitable non-physical way to damage a company – but with the growing demand for analysis and digital transformation, more data in up for grabs than ever before. Consumer behavior towards security is risk-taking, and most consumers only express concerns post attack, assuming that large corporations they share their data with are ‘all-knowing’ and their infrastructures are ‘full-proof’ of sorts.
Most cybercrimes are not even reported, and the element of anonymity adds to the appeal of wanting to hack; as a result, the demand for cybersecurity has never been higher, and will increase proportionally if not more than proportionately (do to exponential risk assumed) as data available for hackers increases. It is a truly ripe space for technological innovation as entrepreneurs hunt for the perfect security solution in a zero sum game where the best infrastructure takes all – hence it is one worth knowing about and watching out for!
This article is the first in a series of articles where the Sutardja Center for Entrepreneurship & Technology takes a basic deep dive into an industry or topic that is at the forefront of startup ideas and opportunities today.
This past week, Yahoo (now owned by Verizon after its highly awaited merger), announced that hackers that had penetrated its network in late 2014 were able to gather information on 500 million users, including their names, email addresses, passwords, telephone numbers and more. Though they clarified that the hackers are no longer ‘believed’ to be able to access their system, the event represents the largest theft of personal data ever. The intrusion came during a period of frequent high-profile hackings, including from companies such as Anthem, MySpace, LinkedIn, Target and Sony – since then, the cybersecurity industry has grown massively, with companies spending millions of dollars to secure their intellectual property, internet platforms and user information. Today, consumers are highly concerned about who has access to their information; having gone through the ‘growth of data’ phase from 2011-2014, where companies focused on easy ways of integrating data, there is no way to trace how many platforms and websites contain a single user’s information, creating the need for individual companies to be highly protective of their data, if they want to keep consumer trust.
Given that we’re in such an era, it is highly important to understand what cybersecurity is, and how it affects us. [Definition] Cyber security involves protecting information and systems from major cyber threats, such as cyber terrorism (cyber terrorism is the disruptive use of information technology by terrorist groups to further their ideological or political agenda), cyber warfare (Cyber warfare involves nation-states using information technology to penetrate another nation’s networks to cause damage or disruption.), and cyber espionage. In their most disruptive form, cyber threats take aim at secret, political, military, or infrastructural assets of a nation, or its people, as well as at monetizable data owned by private companies.
How has cybersecurity changed over the years? Previously, attackers used to largely be creatures of opportunity, looking for the path of least resistance that gave them data – if they encountered secured and protected networks, they were likely to move on and look for softer targets. Today’s cybercriminals are not as defensive; they are highly motivated, well-funded by organizations and structures with agendas, and are more patient in their effort to break into defenses.
[Definition] Malware is malicious software or code that typically damages or disables, takes control of or steals information from a computer system – it may be in the form of adware, backdoors, logic bombs, spyware, Trojan horses or worms (we apologize if that sounds like biology & history more than it does computer science!)
There are various forms of attacks, as defined above – the most prevalent are zero day attacks, that target software vulnerabilities that are yet to be discovered or patched, cloud data leakage which happen when employee uploaded data on servers such as Dropbox and Google Drive are breached or accessible to public and stolen, mobile malware which is specifically intended to steal data on mobile devices (messages, pictures), targeted attacks and SQL injections. The key problem – collectively, advanced malware has outpaced traditional anti‐malware strategies and in the process, has established a foothold within organizations that criminals and nation‐states can use to steal information and attack sensitive assets.
Modern cyberattack strategy has evolved. In addition to direct, open attacks against a high‐value server or asset, today’s attack strategy also employs a patient, multistep, covert process that blends exploits, malware, and evasions in a coordinated attack; these steps include reconnaissance (studying victims and planning attacks, using social engineering, phishing, email address harvesting and other tactics to research and identify targets), weaponization & delivery (determining malware payload, and the method used to deliver it), exploitation, and then installation (which insures persistence of the threat).
To these various forms of attacks, there are a number of prevalent practices for protection – network defenses keep hackers from infiltrating and navigating through corporate networks, endpoint and mobile device protection prevent hackers from compromising individual devices, data in motion defenses protect data while it is being transferred between devices, data at rest defenses protect data when it’s stored in databases & analysis and correlation tools monitor the flow of data to verify that it is being sent or exists only where it should. Each of these defenses represents its own huge industry with a number of players struggling for market share and developing their own versions of solutions for security concerns.
There is an increasing demand for protection against such threats – In 2014, 69% of executives expressed concerned about cyber threats, including a lack of data security, according to a PricewaterhouseCoopers survey. In 2015, an updated survey increased that number to 86%, so it’s clear that the desire for better cybersecurity is not going away anytime soon. Why? The consequences are huge. In addition to commercial losses and public relations problems, disruption of operations and the possibility of extortion, cyber-attacks may also expose an organization to regulatory action, negligence claims, the inability to meet contractual obligations and a damaging loss of trust among customers and suppliers.
The Market for Cybersecurity? BI Analytics estimates that $655Bn will be spent by companies on cybersecurity initiatives to protect PCs ($386Bn), mobile devices ($113Bn) & IoT devices ($172Bn). Research has repeatedly shown that many IoT device manufacturers and service providers are failing to implement common security measures in their products. According to a poll in 2015, 82% of companies expect to be attacked; only 43% of companies feel prepared to deal with such attacks, showing that there is a large addressable market actively in need of a product. There is a large number of companies existing in various offering categories – these can be viewed in the landscape below. Just to begin with, there are 16 major categories of cybersecurity companies can operate in (they can be considered product categories offered by these companies). The largest cybersecurity companies include IBM, Cisco, FireEye, Microsoft, McAfee, CITRIX, Palo Alto Networks, Symantec and money others.
In specific, there is an increasing saturation in cyber security markets by startups themselves in particular. This info graphic shows the saturation of such startups in various markets in just Israel.
One can see clearly that cybersecurity is one of the most important issues prevalent today in the mind of any companies that operate digitally (well, that’s most companies today!). Computer networks have always been a target since it represents the most profitable non-physical way to damage a company – but with the growing demand for analysis and digital transformation, more data in up for grabs than ever before. Consumer behavior towards security is risk-taking, and most consumers only express concerns post attack, assuming that large corporations they share their data with are ‘all-knowing’ and their infrastructures are ‘full-proof’ of sorts.
Most cybercrimes are not even reported, and the element of anonymity adds to the appeal of wanting to hack; as a result, the demand for cybersecurity has never been higher, and will increase proportionally if not more than proportionately (do to exponential risk assumed) as data available for hackers increases. It is a truly ripe space for technological innovation as entrepreneurs hunt for the perfect security solution in a zero sum game where the best infrastructure takes all – hence it is one worth knowing about and watching out for!